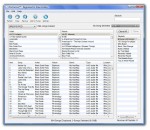
iPod Access is the leading iPod/iPhone music and video transfer application for the PC. With iPod Access you have instant access to all the songs on your iPod and iPhone. Your songs can be be displayed and sorted in almost any fashion so you can find the songs you need right when you need them. With the new instant search feature in v4 you can find songs just as quickly as you would in iTunes.
This software is an utilitarian kid who permits via internet to interrogate the servers of messaging. He/it connects to the server of messaging, post the messages, and indicate to the user numbers it of messages. Very discreet, he/it gets settled as one icon in the rod of the tasks. International languages.
Crobsoft Simple Player support to play Bluray and DVD, and play all format video like mp4/mkv/avi/m4v/mov/mpg, etc. Especially, crobsoft Simple Player support more than 300 video effect filters.
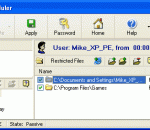
Protect your files from being executed, viewed, changed and deleted. It will automatically enable a chosen protection based on currently logged-in user, current time and the schedule you specify. Disable Internet access, certain games and other software applications during certain periods of time (working hours, for example). Use different sets of applications in different time windows for different users.
Today in the engineered world many users have major problems with the multitude of passwords. With the software abylon LOGON SSO Pro, the user only authenticate once at the windows logon and have additionally an automatic access to password protected applications. The program boasts with high flexibility, centralized administration and enhanced protection against keyloggers and phishing attacks.
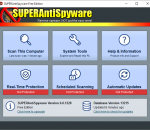
SUPERAntiSpyware is the most thorough scanner on the market. Our Multi-Dimensional Scanning and Process Interrogation Technology will detect the spyware, adware, trojans, ransomware, malware, and infections other products miss! Repair broken Internet Connections, Desktops, Registry Editing and more with our unique Repair System. Dedicated Threat Research Team scours the web for new threats and provides daily definition updates.
REE emergency system repair from a DVD disk or a bootable USB drive to be used if your Windows system is rendered non-bootable by malware. It will help you to not only clean your system of infected and suspicious files but also copy important information to removable media or another computer; Dr.Web LiveDisk also attempts to cure infected objects.
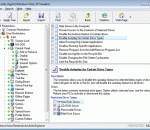
Desktop security solution for personal or publicly accessible computers. It disallows unauthorized changes to various settings of the Windows system, such as Control Panel, Desktop, Local Security Policies, Outlook Express account settings, etc. Disable access to local hard disks, Floppy, CDROM, and removable drives or make them read-only. By locking and hiding or making read-only of programs, files, and folders.
Master Shredder is a files wiping utility. Files deleted by this software cannot be recovered by any third party software or hardware. Master Shredder can securely delete your important files using 18 wiping algorithms, including U.S. DoD 5200.28, NATO Data Destruction Standard, U.S. Air Force Standard, and etc. It also helps you to erase all traces on computer: Typed and visited URLs in IExplorer and FireFox and many other traces.
SafeCrypt is a FIPS 140-2 validated Cloud Encryption Gateway. It allows users to add 256 bit AES encryption to local drives, Google Drive, Dropbox, Bitcasa, OneDrive or most any other cloud storage service. SafeCrypt features include : NIST FIPS 140-2 validation, AES 256 bit encryption, optional 2 factor authentication via Google Authenticator for IOS or Android, and encrypted file names
PDF security removal software allows you to open restricted PDF file. Program authorizes you to crack User and Owner password. Application allows you to insert several PDF file queue for performing operation. You can unlock PDF file just click on Unlock PDF button. After than you can perform appropriates operation on PDF file. Tool allows creating powerful resultant file name with the help on suffix and prefixing operation.
GOM Media Player o único media player precisa - de graça! Não só é GOM Media Player, um reprodutor de vídeo totalmente gratuito, com seu suporte interno para todos os mais populares de vídeo e formatos de Media Player, toneladas de recursos avançados, personalização extrema, e o serviço de localizador de Codec, GOM Media Player é a certo de cumprir todas as suas necessidades de reprodução. Com milhões de usuários em centenas de países, GOM Media Player é um dos players de vídeo mais popular do mundo. O que é novo: Característica de adicionado "configuração de toque" para dispositivos de tela por toque. Adicionado o recurso "Caixa de busca" na lista de reprodução. (Ctrl + F) Suporte "HTTPS URL" para o youtube ou reprodução de rádio líquido. (Ctrl + U) Adicionado "Tocar música" nas preferências relacionadas para reproduzir ficheiros de música. Melhorar o desempenho relacionado a "velocidade de adicionar e excluir" de arquivos na lista de reprodução. Outras correções diversas, correções e alterações
O Iperius Backup é um dos melhores softwares de backup gratuitos, também lançado em edições comerciais para aqueles que precisam de recursos de backup avançados para suas empresas. A versão grátis do Iperius Backup permite fazer backup para qualquer dispositivo de armazenamento em massa, como o NAS, discos rígidos externos USB, discos de RDX, e computadores em rede. Tem funções de envio de e-mail a programação completa e. Ele suporta compactação zip sem limite de tamanho, backup incremental, autenticação de rede e execução de scripts externos e programas.
MaryFi é um roteador de software livre e fácil de usar para computadores Windows 7, 8 e 8.1. Com Maryfi, os usuários podem sem fio compartilhar qualquer conexão de Internet tais como: um modem de cabo, um cartão de celular ou mesmo outra rede Wi-Fi. Outros dispositivos Wi-Fi habilitado, incluindo laptops, smartphones, players de música e sistemas de jogos podem ver e juntar o seu hotspot Maryfi apenas como qualquer outro ponto de acesso Wi-Fi e são mantidos seguros e protegidos pelo protegido por senha de criptografia WPA2.