Edit MPEG, AVI, DVD, Blu-ray, HD, WMV, etc. without reconversion with AVS Video ReMaker. Cut, trim, remove unwanted video parts and save your video anew. No quality loss! Create and add DVD/Blu-ray menus. Capture video from camcorders, video cameras and web cameras. AVS Video ReMaker is a part of AVS4YOU.com package. Register once at avs4you.com and use all tools from the AVS4YOU.com package. Subscribe for $39/year or $59/lifetime.
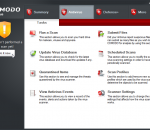
Comodo AntiVirus leverages multiple technologies (including on demand & on access scanning, email scanning, process monitoring, worm blocking and host intrusion prevention) to immediately start cleaning or quarantining suspicious files from your hard drives, shared disks, emails, downloads and system memory.
Encrypt and convert CHM to exe with password protected, prevent from editing, copying and printing. You can only convert chm to exe without password, and you can also set a password with PC-binding to your users. Only you can create open password for your users. Easily distribute CHM files and protect it.
WinX Free AVI to 3GP Converter is a free video converter that converts AVI videos to 3GP. It provides you faster AVI video to 3GP video converting speed when compared with same AVI to 3GP video converters in market. Besides converting AVI to 3GP, users can free trim the video clips as the target converting video and adjust the video/audio parameters. 100% Clean, No Spyware, No Malware, No Adware and No Virus.
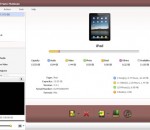
AVCWare iPad Mate Platinum, the all-in-one iPad content transfer/converter/manager, allows you to manage iPad contents in the round: transfer iPad music/movies/eBooks/photos/ringtones to PC and vice versa, copy iPad multimedia files to iTunes for backup, rip CDs/DVDs to iPad supported files, convert non-iPad video/audio files and transfer them to iPad directly after conversion.
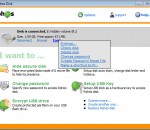
Rohos Disk - program creates hidden and protected partitions on the computer or USB flash drive. Those who have megabytes of sensitive files and seriously concerned with data security, can not imagine their computer or USB drive without the hidden partition that is created using this wonderful tool.
Phoscyon x64 is a vintage analog modeled Bassline synthesizer with a unique low pass filter with an 18db/oct dumping and constant resonance amplitude throughout the entire frequency domain. The filter sounds phenomenal! Hear that squelch and you’ll swear its analog! We’ve also equipped it with a fully customizable integrated arpeggiator (essential in electronic music) as well as an exhaustively analog modeled distortion effect.
VSCryptoHash is cryptographic hash calculation software. Simply drag and drop files (or type the text) in this calculator and hash string for the files (or for entered text) will be immediately displayed. It is Great tool for network administrators and webmasters to calculate file control sums. VSCryptoHash supports a variety of cryptographic hash functions, including SHA-1, SHA-256, SHA-384, SHA-512, MD5, MD4 and MD2.
Do you want to protect private pictures, hide sensitive videos or lockdown documents ? Do you want to ensure your privacy by locking, hiding and encrypting sensitive data ? Then this free application is for you.Quick File Locker will quickly lock, hide and encrypt files, folders or USB drives to ensure your privacy. It is very easy to use.Lock files with a simple drag and drop or with a right click on them in Windows Explorer. Multilingual.
What is Screen Monitor? Screen Monitor is tool software that can monitor what others do on your computer. It can periodically capture screen shots, and determine whether the same as the last screenshot, if different, save the screenshot. How to install? You dont need install. Only unzip sm.zip, then run the sm.exe. How to start monitoring? Very simple, just click on the Start Monitor button, and then click Hide button.
SoundObjects are the building blocks within blue's score timeline. SoundObjects can be lists of notes, algorithmic generators, python script code, Csound instrument definitions, PianoRolls, Pattern Editors, Tracker interfaces, and more. These soundObjects may be text based or GUI-based as well.
GOM Media Player o único media player precisa - de graça! Não só é GOM Media Player, um reprodutor de vídeo totalmente gratuito, com seu suporte interno para todos os mais populares de vídeo e formatos de Media Player, toneladas de recursos avançados, personalização extrema, e o serviço de localizador de Codec, GOM Media Player é a certo de cumprir todas as suas necessidades de reprodução. Com milhões de usuários em centenas de países, GOM Media Player é um dos players de vídeo mais popular do mundo. O que é novo: Característica de adicionado "configuração de toque" para dispositivos de tela por toque. Adicionado o recurso "Caixa de busca" na lista de reprodução. (Ctrl + F) Suporte "HTTPS URL" para o youtube ou reprodução de rádio líquido. (Ctrl + U) Adicionado "Tocar música" nas preferências relacionadas para reproduzir ficheiros de música. Melhorar o desempenho relacionado a "velocidade de adicionar e excluir" de arquivos na lista de reprodução. Outras correções diversas, correções e alterações
O Iperius Backup é um dos melhores softwares de backup gratuitos, também lançado em edições comerciais para aqueles que precisam de recursos de backup avançados para suas empresas. A versão grátis do Iperius Backup permite fazer backup para qualquer dispositivo de armazenamento em massa, como o NAS, discos rígidos externos USB, discos de RDX, e computadores em rede. Tem funções de envio de e-mail a programação completa e. Ele suporta compactação zip sem limite de tamanho, backup incremental, autenticação de rede e execução de scripts externos e programas.
MaryFi é um roteador de software livre e fácil de usar para computadores Windows 7, 8 e 8.1. Com Maryfi, os usuários podem sem fio compartilhar qualquer conexão de Internet tais como: um modem de cabo, um cartão de celular ou mesmo outra rede Wi-Fi. Outros dispositivos Wi-Fi habilitado, incluindo laptops, smartphones, players de música e sistemas de jogos podem ver e juntar o seu hotspot Maryfi apenas como qualquer outro ponto de acesso Wi-Fi e são mantidos seguros e protegidos pelo protegido por senha de criptografia WPA2.